Kubernetes
一、基础知识
1. 概念和术语
2. Kubernetes特性
3. 集群组件
4. 抽象对象
5. 镜像加速下载
二、安装部署kubeadm
1. 基础环境准备
2. 安装runtime容器(Docker)
3. 安装runtime容器(Contained)
4. Containerd进阶使用
5. 部署kubernets集群
6. 部署calico网络组件
7. 部署NFS文件存储
8. 部署ingress-nginx代理
9. 部署helm包管理工具
10. 部署traefik代理
11. 部署dashboard管理面板(官方)
12. 部署kubesphere管理面板(推荐)
12. 部署metrics监控组件
13. 部署Prometheus监控
14. 部署elk日志收集
15. 部署Harbor私有镜像仓库
16. 部署minIO对象存储
17. 部署jenkins持续集成工具
三、kubectl命令
1. 命令格式
2.node操作常用命令
3. pod常用命令
4.控制器常用命令
5.service常用命令
6.存储常用命令
7.日常命令总结
8. kubectl常用命令
四、资源对象
1. K8S中的资源对象
2. yuml文件
3. Kuberbetes YAML 字段大全
4. 管理Namespace资源
5. 标签与标签选择器
6. Pod资源对象
7. Pod生命周期与探针
8. 资源需求与限制
9. Pod服务质量(优先级)
五、资源控制器
1. Pod控制器
2. ReplicaSet控制器
3. Deployment控制器
4. DaemonSet控制器
5. Job控制器
6. CronJob控制器
7. StatefulSet控制器
8. PDB中断预算
六、Service和Ingress
1. Service资源介绍
2. 服务发现
3. Service(ClusterIP)
4. Service(NodePort)
5. Service(LoadBalancer)
6. Service(ExternalName)
7. 自定义Endpoints
8. HeadlessService
9. Ingress资源
10. nginx-Ingress案例
七、Traefik
1. 知识点梳理
2. 简介
3. 部署与配置
4. 路由(IngressRoute)
5. 中间件(Middleware)
6. 服务(TraefikService)
7. 插件
8. traefikhub
9. 配置发现(Consul)
10. 配置发现(Etcd)
八、存储
1. 配置集合ConfigMap
6. downwardAPI存储卷
3. 临时存储emptyDir
2. 敏感信息Secret
5. 持久存储卷
4. 节点存储hostPath
7. 本地持久化存储localpv
九、rook
1. rook简介
2. ceph
3. rook部署
4. rbd块存储服务
5. cephfs共享文件存储
6. RGW对象存储服务
7. 维护rook存储
十、网络
1. 网络概述
2. 网络类型
3. flannel网络插件
4. 网络策略
5. 网络与策略实例
十一、安全
1. 安全上下文
2. 访问控制
3. 认证
4. 鉴权
5. 准入控制
6. 示例
十二、pod调度
1. 调度器概述
2. label标签调度
3. node亲和调度
4. pod亲和调度
5. 污点和容忍度
6. 固定节点调度
十三、系统扩展
1. 自定义资源类型(CRD)
2. 自定义控制器
十四、资源指标与HPA
1. 资源监控及资源指标
2. 监控组件安装
3. 资源指标及其应用
4. 自动弹性缩放
十五、helm
1. helm基础
2. helm安装
3. helm常用命令
4. HelmCharts
5. 自定义Charts
6. helm导出yaml文件
十六、k8s高可用部署
1. kubeadm高可用部署
2. 离线二进制部署k8s
3. 其他高可用部署方式
十七、日常维护
1. 修改节点pod个数上限
2. 集群证书过期更换
3. 更改证书有效期
4. k8s版本升级
5. 添加work节点
6. master节点启用pod调度
7. 集群以外节点控制k8s集群
8. 删除本地集群
9. 日常错误排查
10. 节点维护状态
11. kustomize多环境管理
12. ETCD节点故障修复
13. 集群hosts记录
14. 利用Velero对K8S集群备份还原与迁移
15. 解决K8s Namespace无法正常删除的问题
16. 删除含指定名称的所有资源
十八、k8s考题
1. 准备工作
2. 故障排除
3. 工作负载和调度
4. 服务和网络
5. 存储
6. 集群架构、安装和配置
本文档使用 MrDoc 发布
-
+
首页
9. 配置发现(Consul)
# 配置发现简介 traefik除了可以对接kubernetes ingressroute外,也支持其他常用的服务发现中间件,例如consul、etcd、zookeeper等。以consul为例,我们只需要向consul中注册服务,traefik监听到有新的服务注册时,会实时检测服务并自动更新路由规则。<br />参考文档:[https://doc.traefik.io/traefik/providers/overview/](https://doc.traefik.io/traefik/providers/overview/)<br /> # k8s部署consul ## helm安装consul 参考文档:[https://developer.hashicorp.com/consul/tutorials/kubernetes/kubernetes-deployment-guide](https://developer.hashicorp.com/consul/tutorials/kubernetes/kubernetes-deployment-guide)<br />版本要求:k8s版本:1.21.0+,helm版本3.2.1+<br />配置Helm Chart ```bash # 添加repo [root@k8s-master ~]# helm repo add hashicorp https://helm.releases.hashicorp.com "hashicorp" has been added to your repositories # 更新repo仓库资源 [root@k8s-master ~]# helm repo update Hang tight while we grab the latest from your chart repositories... ...Successfully got an update from the "hashicorp" chart repository ...Successfully got an update from the "stable" chart repository Update Complete. ⎈Happy Helming!⎈ # 查看consul可用版本信息 [root@k8s-master ~]# helm search repo consul NAME CHART VERSION APP VERSION DESCRIPTION hashicorp/consul 0.49.0 1.13.2 Official HashiCorp Consul Chart stable/consul 3.9.6 1.5.3 Highly available and distributed service discov... stable/prometheus-consul-exporter 0.1.6 0.4.0 DEPRECATED A Helm chart for the Prometheus Cons... # 拉取helm包资源 [root@k8s-master ~]# helm pull hashicorp/consul [root@k8s-master ~]# ls anaconda-ks.cfg consul-0.49.0.tgz # 解压查看 [root@k8s-master ~]# tar -zxf consul-0.49.0.tgz [root@k8s-master ~]# ls anaconda-ks.cfg consul consul-0.49.0.tgz ``` ## 创建存储资源 查看value.yaml配置文件可知,部署的时候会创建使用 PVC:PersistentVolumeClaim 的 Pod ,Pod 中的应用通过 PVC 进行数据的持久化,而 PVC 使用 PV: PersistentVolume 进行数据的最终持久化处理。所以我们要准备好存储资源供应,否则 consul会因为获取不到存储资源而一直处于 pending 状态。 ```bash [root@k8s-master ~]# cd consul/ [root@k8s-master consul]# cat values.yaml # This defines the disk size for configuring the # servers' StatefulSet storage. For dynamically provisioned storage classes, this is the # desired size. For manually defined persistent volumes, this should be set to # the disk size of the attached volume. storage: 10Gi # The StorageClass to use for the servers' StatefulSet storage. It must be # able to be dynamically provisioned if you want the storage # to be automatically created. For example, to use # local(https://kubernetes.io/docs/concepts/storage/storage-classes/#local) # storage classes, the PersistentVolumeClaims would need to be manually created. # A `null` value will use the Kubernetes cluster's default StorageClass. If a default # StorageClass does not exist, you will need to create one. # Refer to the [Read/Write Tuning](https://www.consul.io/docs/install/performance#read-write-tuning) # section of the Server Performance Requirements documentation for considerations # around choosing a performant storage class. # # ~> **Note:** The [Reference Architecture](https://learn.hashicorp.com/tutorials/consul/reference-architecture#hardware-sizing-for-consul-servers) # contains best practices and recommendations for selecting suitable # hardware sizes for your Consul servers. # @type: string storageClass: null ``` 我们可以手动创建静态pv或者使用StorageClass动态卷供应实现存储持久化,为了方便演示,此处以最简单的静态PV为例。 ```bash [root@k8s-master consul]# cat pv.yaml apiVersion: v1 kind: PersistentVolume metadata: name: consul-pv-0 spec: storageClassName: "" capacity: storage: 10Gi accessModes: - ReadWriteOnce persistentVolumeReclaimPolicy: Delete hostPath: path: "/data/consul" type: DirectoryOrCreate nodeAffinity: required: nodeSelectorTerms: - matchExpressions: - key: kubernetes.io/hostname operator: In values: - k8s-master --- apiVersion: v1 kind: PersistentVolume metadata: name: consul-pv-1 spec: storageClassName: "" capacity: storage: 10Gi accessModes: - ReadWriteOnce persistentVolumeReclaimPolicy: Delete hostPath: path: "/data/consul" type: DirectoryOrCreate nodeAffinity: required: nodeSelectorTerms: - matchExpressions: - key: kubernetes.io/hostname operator: In values: - k8s-work1 --- apiVersion: v1 kind: PersistentVolume metadata: name: consul-pv-2 spec: storageClassName: "" capacity: storage: 10Gi accessModes: - ReadWriteOnce persistentVolumeReclaimPolicy: Delete hostPath: path: "/data/consul" type: DirectoryOrCreate nodeAffinity: required: nodeSelectorTerms: - matchExpressions: - key: kubernetes.io/hostname operator: In values: - k8s-work2 [root@k8s-master consul]# kubectl apply -f pv.yaml persistentvolume/consul-pv-0 created persistentvolume/consul-pv-1 created persistentvolume/consul-pv-2 created [root@k8s-master consul]# kubectl get pv NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS REASON AGE consul-pv-0 10Gi RWO Delete Available 4s consul-pv-1 10Gi RWO Delete Available 4s consul-pv-2 10Gi RWO Delete Available 4s ``` ## 部署consul资源 修改helm变量配置 ```bash global: name: consul # 设置用于 Helm chart 中所有资源的前缀 ui: service: # 为 Consul UI 配置服务 type: "NodePort" # 服务类型为 NodePort server: replicas: 3 # 要运行的服务器的数量,即集群数 storage: '10Gi' # 定义用于配置服务器的 StatefulSet 存储的磁盘大小 storageClass: "" # 使用Kubernetes集群的默认 StorageClass securityContext: # 服务器 Pod 的安全上下文,以 root 用户运行 fsGroup: 2000 runAsGroup: 2000 runAsNonRoot: false runAsUser: 0 ``` 创建资源 ```bash [root@k8s-master consul]# helm install consul hashicorp/consul -n consul -f values.yaml --create-namespace [root@k8s-master consul]# helm list -n consul NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION consul consul 1 2022-10-28 10:43:56.104694201 +0800 CST deployed consul-0.49.0 1.13.2 ``` # 访问验证 ## 查看资源信息 ```bash [root@k8s-master consul]# kubectl get pod -n consul NAME READY STATUS RESTARTS AGE consul-client-78jzj 1/1 Running 0 3m12s consul-client-dhtxw 1/1 Running 0 80s consul-client-mm6hf 1/1 Running 0 3m12s consul-server-0 1/1 Running 0 3m12s consul-server-1 1/1 Running 0 3m12s consul-server-2 1/1 Running 0 3m12s [root@k8s-master consul]# kubectl get svc -n consul NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE consul-dns ClusterIP 10.108.192.200 <none> 53/TCP,53/UDP 4m5s consul-server ClusterIP None <none> 8500/TCP,8503/TCP,8301/TCP,8301/UDP,8302/TCP,8302/UDP,8300/TCP,8600/TCP,8600/UDP 4m5s consul-ui NodePort 10.99.86.8 <none> 80:32177/TCP 4m5s 104s ``` ## nodeport方式访问consul 根据service信息可知,consul-ui服务的80端口映射在k8s节点的31277端口,直接访问k8s节点ip:31277即可<br /> ## ingress方式访问consul-ui 创建ingressroute资源 ```yaml [root@k8s-master consul]# cat ingress.yaml apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: consul-ui namespace: consul spec: entryPoints: - web routes: - match: Host(`consul-ui.test.com`) kind: Rule services: - name: consul-ui port: 80 namespace: consul [root@k8s-master consul]# kubectl apply -f ingress.yaml ingressroute.traefik.containo.us/consul-ui created ``` 添加hosts解析记录`192.168.93.128 consul-ui.test.com`,然后访问consul-ui.test.com<br /> # traefik对接consul 参考文档:[https://doc.traefik.io/traefik/providers/consul-catalog/](https://doc.traefik.io/traefik/providers/consul-catalog/) ## traefik启用consul配置发现 修改traefik配置,添加consulCatalog相关配置。 ```yaml [root@k8s-master traefik]# cat traefik-config.yaml apiVersion: v1 kind: ConfigMap metadata: name: traefik-config namespace: traefik data: traefik.yaml: |- global: checkNewVersion: false # 周期性的检查是否有新版本发布 sendAnonymousUsage: false # 周期性的匿名发送使用统计信息 serversTransport: insecureSkipVerify: true # Traefik忽略验证代理服务的TLS证书 api: insecure: true # 允许HTTP 方式访问API dashboard: true # 启用Dashboard debug: false # 启用Debug调试模式 metrics: prometheus: # 配置Prometheus监控指标数据,并使用默认配置 addRoutersLabels: true # 添加routers metrics entryPoint: "metrics" # 指定metrics监听地址 entryPoints: web: address: ":80" # 配置80端口,并设置入口名称为web forwardedHeaders: insecure: true # 信任所有的forward headers websecure: address: ":443" # 配置443端口,并设置入口名称为 websecure forwardedHeaders: insecure: true traefik: address: ":9000" # 配置9000端口,并设置入口名称为 dashboard metrics: address: ":9100" # 配置9100端口,作为metrics收集入口 tcpep: address: ":9200" # 配置9200端口,作为tcp入口 udpep: address: ":9300/udp" # 配置9300端口,作为udp入口 providers: kubernetesCRD: # 启用Kubernetes CRD方式来配置路由规则 ingressClass: "" # 指定traefik的ingressClass名称 allowCrossNamespace: true #允许跨namespace allowEmptyServices: true #允许空endpoints的service consulCatalog: # 启用consul服务发现 endpoint: # consul服务地址 address: consul-server.consul.svc:8500 log: filePath: "/etc/traefik/logs/traefik.log" # 设置调试日志文件存储路径,如果为空则输出到控制台 level: "DEBUG" # 设置调试日志级别 format: "common" # 设置调试日志格式 accessLog: filePath: "/etc/traefik/logs/access.log" # 设置访问日志文件存储路径,如果为空则输出到控制台 format: "common" # 设置访问调试日志格式 bufferingSize: 0 # 设置访问日志缓存行数 filters: # statusCodes: ["200"] # 设置只保留指定状态码范围内的访问日志 retryAttempts: true # 设置代理访问重试失败时,保留访问日志 minDuration: 20 # 设置保留请求时间超过指定持续时间的访问日志 fields: # 设置访问日志中的字段是否保留(keep保留、drop不保留) defaultMode: keep # 设置默认保留访问日志字段 names: # 针对访问日志特别字段特别配置保留模式 ClientUsername: drop StartUTC: drop # 禁用日志timestamp使用UTC headers: # 设置Header中字段是否保留 defaultMode: keep # 设置默认保留Header中字段 names: # 针对Header中特别字段特别配置保留模式 # User-Agent: redact# 可以针对指定agent Authorization: drop Content-Type: keep [root@k8s-master traefik]# kubectl apply -f traefik-config.yaml configmap/traefik-config configured ``` 访问traefik dashboard,查看providers信息<br /> ## 创建测试资源 创建测试应用 ```yaml [root@k8s-master k8s-test]# cat whoami.yaml apiVersion: apps/v1 kind: Deployment metadata: name: whoami spec: selector: matchLabels: app: whoami template: metadata: labels: app: whoami spec: containers: - name: whoami image: traefik/whoami resources: limits: memory: "128Mi" cpu: "500m" ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: whoami spec: selector: app: whoami ports: - port: 80 targetPort: 80 [root@k8s-master k8s-test]# kubectl apply -f whoami.yaml deployment.apps/whoami created service/whoami created [root@k8s-master k8s-test]# kubectl get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE whoami ClusterIP 10.100.157.68 <none> 80/TCP 44s [root@k8s-master k8s-test]# kubectl get pod whoami-b885f644f-lz7sj 1/1 Running 0 49s ``` 创建base auth认证中间件 ```yaml [root@k8s-master auth]# cat basic-auth-middleware.yaml apiVersion: traefik.containo.us/v1alpha1 kind: Middleware metadata: name: basic-auth-middleware spec: basicAuth: secret: basic-auth [root@k8s-master auth]# kubectl apply -f basic-auth-middleware.yaml middleware.traefik.containo.us/basic-auth-middleware created ``` ## 注册服务到consul ```bash [root@test /]# curl -X PUT -d '{"name":"whoami","address":"whoami.default.svc","port":80,"tags":["traefik.http.routers.whoami.rule=Host(`whoami.test.com`)","traefik.http.routers.whoami.entrypoints=web","traefik.http.routers.whoami.middlewares=default-basic-auth-middleware@kubernetescrd"]}' http://consul-server.consul.svc:8500/v1/agent/service/register ``` 参数说明:<br />address:service资源地址<br />tags:traefik相关配置 ```bash traefik.http.routers.whoami.rule=Host(`whoami.test.com`):指定ingressroute路径 traefik.http.routers.whoami.entrypoints=web:指定endpoints类型 traefik.http.routers.whoami.middlewares=default-basic-auth-middleware@kubernetescrd:指定中间件 ``` ## 访问验证 查看consul-ui信息,服务已成功注册。<br />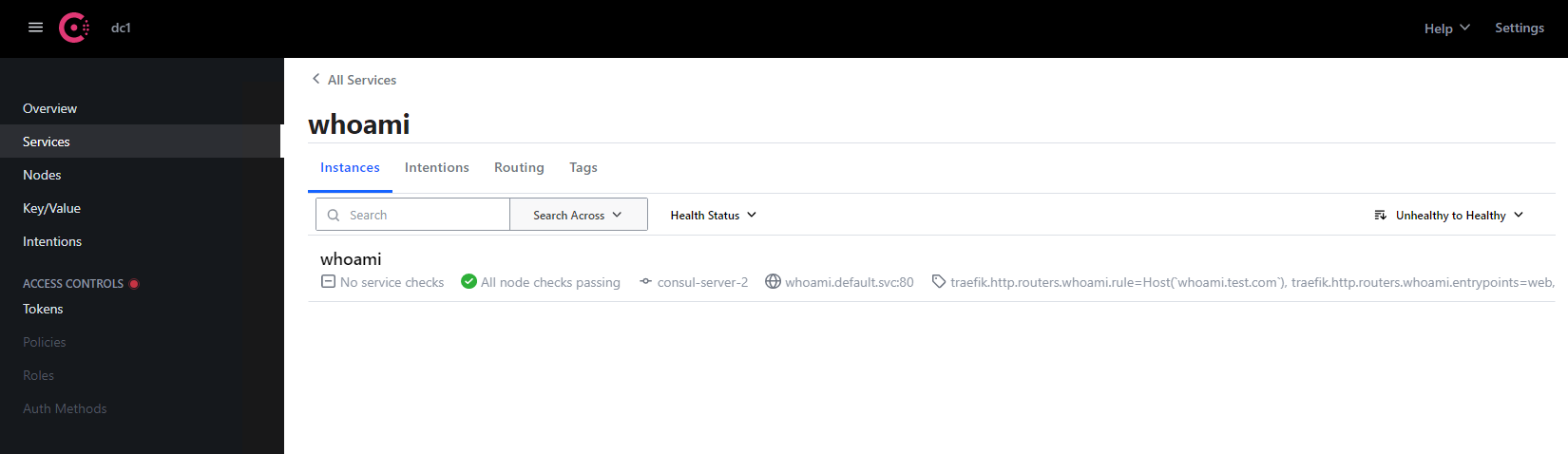<br />查看traefik dashboard,已自动添加路由规则,并配置了base auth认证中间件。<br /><br />访问验证,添加hosts记录,访问`whoami.test.com`<br />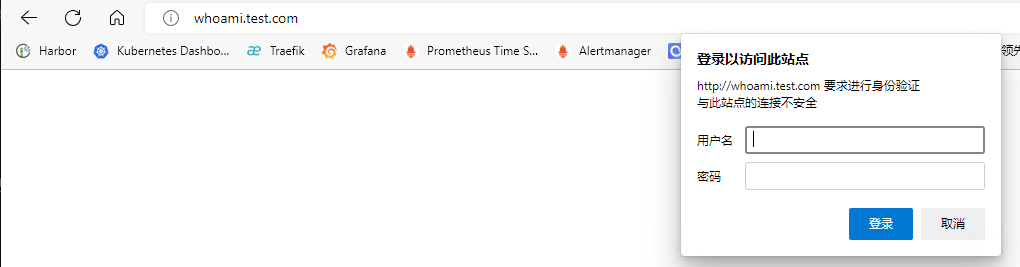<br />输入账号密码后成功访问whoami应用<br />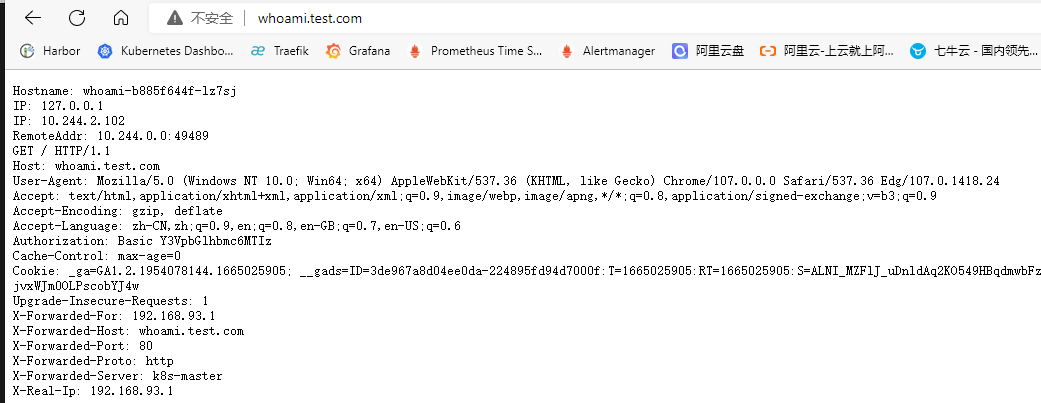<br />[<br />](https://nosaid.com/article/use-traefik#%E6%B5%81%E9%87%8F%E6%B5%81%E8%BD%AC)
Nathan
2024年6月22日 12:47
转发文档
收藏文档
上一篇
下一篇
手机扫码
复制链接
手机扫一扫转发分享
复制链接
Markdown文件
PDF文件
Docx文件
分享
链接
类型
密码
更新密码